Allow Syncing Only on PCs Joined to Specific Domains in Office 365

Microsoft Office 365 has a nice security feature as a syncing option in Office 365 OneDrive admin center called “Allow Syncing Only on PCs Joined to Specific Domains.” This feature can be configured by the Office 365 Global Administrator. You will find this option listed in OneDrive admin center under the Sync category. It restricts the syncing of OneDrive content to only domain-joined PCs to enhance security.
Here’s how you can configure this feature.
- Logon to Office 365 as a Global Administrator at https://portal.office.com.
- Go to the Admin centers and then click OneDrive.
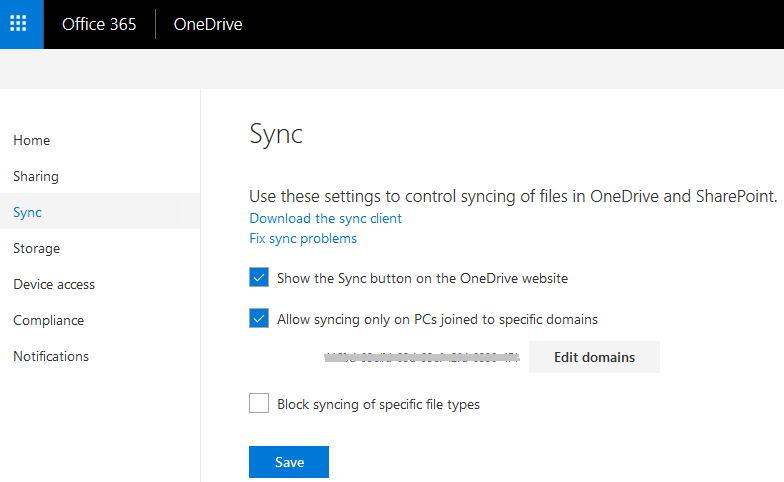
- From the Home screen in OneDrive admin center click Sync.
- You will see the following three options:
a) Show the Sync button on the OneDrive website
b) Allow syncing only on PCs joined to specific domains
c) Block syncing of specific file types
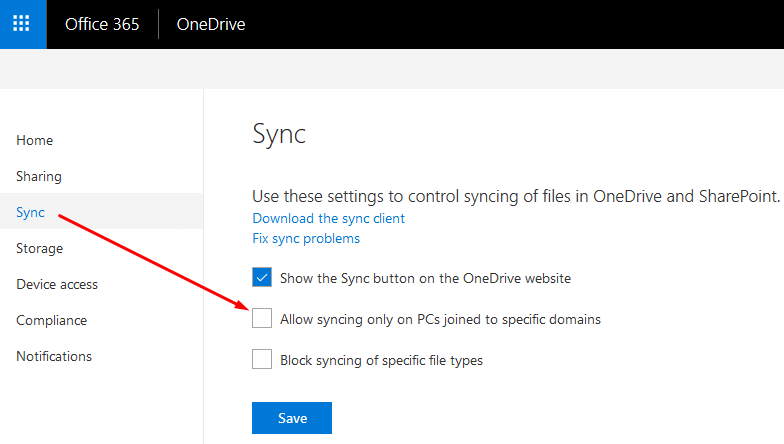
- The first option is selected by default. Select the second option Allow syncing only on PCs joined to specific domains. This option can restrict syncing of OneDrive data only to computers that have joined your domain.
- Click Edit domains and specify which domains should be allowed syncing of content. Clients who have joined any domains that are not listed here will be prevented from syncing OneDrive data. This seems pretty straight forward, but there is something you should know about this feature. When you click Edit domains, you will see the following box.
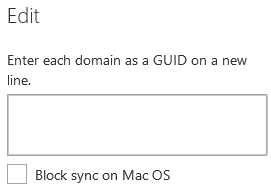
This step can be tricky if you don’t know what you need to do here. Because you are working in Office 365, obviously you are going to enter the domain Globally Unique Identifier (GUID) for your Office 365 domain. Right? Not exactly! You are supposed to enter the domain GUID for your on-premises Active Directory domain here. I know it’s confusing because there is nothing in the instructions you will find that gives you the impression that this feature only works with on-premises Active Directory.
NOTE: A GUID is a 128-bit number used to uniquely identify each object in Active Directory. Unlike a Security Identifier (SID), which can potentially change , a GUID never changes and is unique not just across the enterprise, but according to Microsoft it’s unique across the world. - Run the Get-ADDomain on your Domain Controller or a member server to get the domain GUID. Look for the ObjectGUID entry in the results. You can also run Get-ADDomain on your domain-joined workstation if you have the Active Directory PowerShell Module installed, but it’s much easier to get the domain GUID from your server.
- You can add the GUID for additional Active Directory on-premises domains, if necessary. Just remember to press the Enter key after each entry. Once you add the GUID and close the Edit domains box, you will see your domain GUID(s) added.
- Click Save to keep your changes.
- It can take at least an hour before the configuration takes effect and the feature will work.
It’s unfortunate that this feature only works with on-premises Active Directory. There are many small businesses around the world that don’t have an on-premises Active Directory domain and would therefore be unable to take advantage of this feature. It would be nice if Microsoft adds the words on-premises or local domain somewhere in the Edit box. For example, updating the instructions and adding the words in bold would be helpful in avoiding confusion:
| This feature works with on-premises Active Directory domains. Enter each on-premises domain as a GUID on a new line. Use the PowerShell command Get-ADDomain on your domain server to get the domain GUID. |
This Microsoft article contains a link on how to find the domain GUID, but the information applies to a local on-premises Active Directory. Organizations that don’t have on-premises Active Directory have difficulty figuring out how to use this article and find their domain GUID. I have provided my feedback to Microsoft. Hopefully, Microsoft will allow us to use this feature with domains in Office 365 in the future, or at least make it clear in the instructions that this OneDrive feature is limited to on-premises domains.
| Thanks for reading my article. If you are interested in IT training & consulting services, please reach out to me. Visit ZubairAlexander.com for information on my professional background. |
Copyright © 2018 SeattlePro Enterprises, LLC. All rights reserved.



Just wanted to say thanks for the article. I got hung up on the domain GUID like you mentioned and this helped.
Thanks for the feedback, David. As I mentioned in my article, entering the GUID can be tricky because you are not told which domain GUID you need.
What if your endpoints are Azure AD joined and no longer talk to the on-premises AD directly? Does this make a difference? Could the Azure AD Directory ID not then work here? As it is in the exact format. XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX
Louis, at the time I wrote this article last year, only on-premises domains were allowed. Therefore, Azure AD ID won’t work, even if it is in the exact format. That was the only reason I wrote this article. If your experience is different, please let me know.
I can not gt this to work consistently.
I have a PC joined to the domain that cannot download or sync onedrive or sharepoint files. I have a PC NOT joined to any domain that CAN download or sync onedrive or sharepoint files.
If I refresh my browser page (F5) this restriction is added, then removed, in other words its toggled.
I am logged into both PC’s (joined and not joined) with the same global admin account
Any ideas what is going on?
Simon, you may multiple OneDrives installed on your computer. This is often the case if you are running Windows 10 and Microsoft Office, and are also connected to Office 365. Check out my article How to Identify the Various Versions of OneDrive on Your Computer. You may also be interested in another article How to Disable or Remove OneDrive in Windows 10. Good luck!
Hi. Do you know what happen with the OneDrive client for iOS or Android. Can files be seen on those devices if the Allow sync is activated for specific domains?
I have the same question as @Dan; If enabled and configured, does this option applies to mobile devices, iPads, etc.?