Understanding and Configuring the App Password in Microsoft 365

Multi-Factor Authentication (MFA) in Microsoft 365 (formerly known as Microsoft Office 365) has several advantages. Once you enable MFA, it offers a much higher level of security because users can secure their credentials with a second level of authentication, such as:
- Call to phone
- Text message to phone
- Notification through mobile app
- Verification code from mobile app or hardware token
An important concept that is not usually clear to people who are new to Microsoft 365 is the concept of App Password, short for application password. This only comes into play when MFA is enabled. Once the MFA is turned on, a user can utilize the username/password combination as the first authentication factor and one of the above listed options as a second factor to sign in to Microsoft 365. However, the user can run into a problem when a non-browser application is used with Microsoft 365, such as Outlook 2013 client or Apple Mail. To accommodate such scenarios, Microsoft offers app passwords that are used to essentially bypass the use of MFA for the non-browser applications. Keep in mind that the app password is tied to the user’s account in Microsoft 365 portal so this password cannot be generated outside of Microsoft 365 because it’s stored in Azure.
Allowing Users to Create App Passwords
A Global Admin in Microsoft 365 can decide whether to allow users to create the app passwords. Here’s how you can enable this feature.
- Log in to Microsoft 365 admin center as a Global Admin at https://portal.office.com/adminportal/home.
- Under the Users section, click Active users.
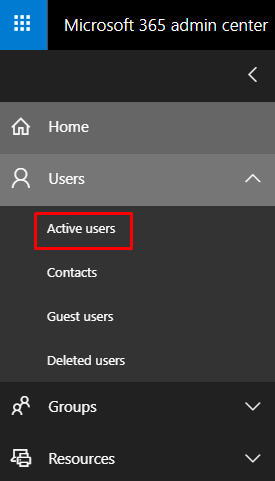
- Click More and select Multifactor Authentication setup.
NOTE: The word Multi-factor is spelled inconsistently throughout Microsoft 365. A vast majority of Microsoft documents spell it with a hyphen.
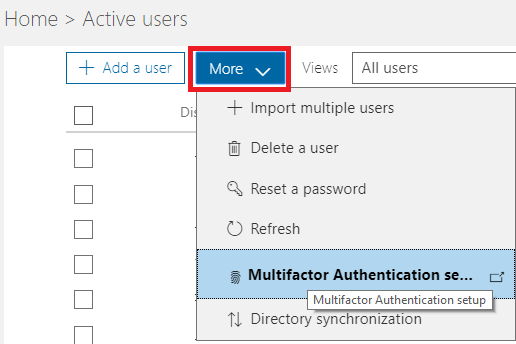
- The Multi-factor authentication page has two tabs (a users tab and service settings tab), but it’s not quite obvious because not only the tabs are not colored, the tab headings are all in lowercase so it’s not easy to differentiate them from the rest of the text. Click on the users tab first, then we will look at the service settings tab.
- On the users tab, you can configure MFA settings for one or more users. Under quick steps, you can either Enable the MFA for the user, or Manage user settings. Managing settings gives you the following three options.
– Require selected users to provide contact methods again
– Delete all existing app passwords generated by the selected users
– Restore multi-factor authentication on all remembered devices
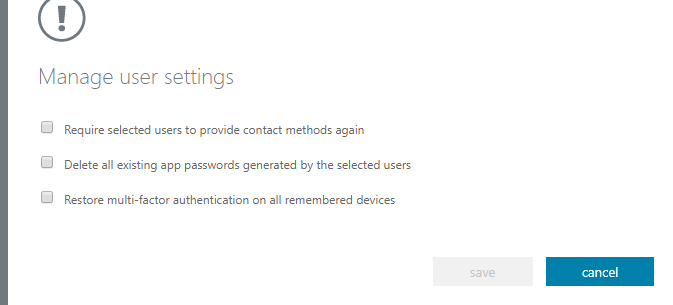
The center option will allow you to delete existing app passwords generated by the user. This can come handy when a user is having issues with logging in to non-browser client apps used with Microsoft 365. For example, if you want to delete the app passwords for five different users, simply select those five accounts and delete the existing app passwords generated by them. This will allow them to generate new passwords. - Now select the service settings tab. This is where you can enable the option Allow users to create app passwords to sign in to non-browser apps. If this radio button is not selected, the users will be unable to create a password for their non-browser apps so it’s important that whenever you enable MFA, make sure this option is selected, unless you have a valid reason to prevent them from creating app passwords.
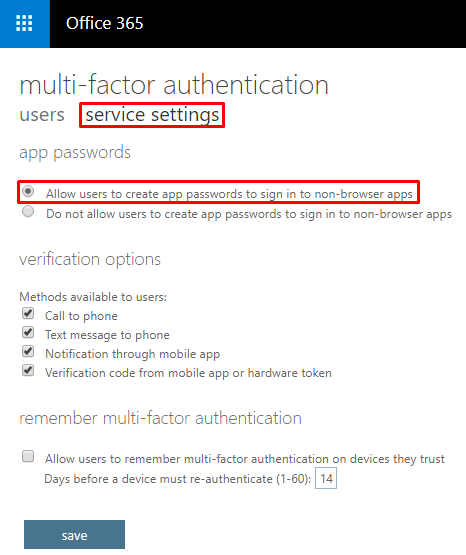
- Configure the verification options as necessary and then click Save to apply the settings.
- When the users sign in to Microsoft 365 after the Global Admin has enabled the MFA, they will see the notice on the sign in screen Your admin has required that you set up this account for additional security verification and a blue button that says Set it up now. They can follow the on-screen instructions and within a few mouse clicks generate an app password.
| NOTE: There’s no need for users to create an app password for Office 2016 clients, such as Outlook 2016, because MFA is supported by Office 2016 client apps. |
If you are having problems with the 2-step verification method in Microsoft 365, such as users not getting the verification code on their mobile phone or not getting prompted for a second verification, visit Fix common problems with 2-step verification.
| Thanks for reading my article. If you are interested in IT training & consulting services, please reach out to me. Visit ZubairAlexander.com for information on my professional background. |
Copyright © 2018 SeattlePro Enterprises, LLC. All rights reserved.



Deepnet Security has now created a new web page dedicated to hardware tokens for Azure MFA and Office 365, and provides information of how to use SafeID tokens with Azure MFA (see following link);
http://www.deepnetsecurity.com/authenticators/one-time-password/safeid/hardware-mfa-tokens-office-365-azure-multi-factor-authentication/