Understanding PowerShell Execution Policies on Windows Platforms

To prevent Windows 10 clients from running malicious scripts on Windows computers, you can configure a PowerShell execution policy. The policy essentially controls how the PowerShell configuration files are loaded. Just to be clear, this is not some kind of built-in security feature that will block users from running PowerShell commands. For example, if a user wants to run a script that has ten PowerShell commands in it, she can’t execute the script from the PowerShell console or at the Command Prompt. However, she can execute the ten individual PowerShell commands within the script one at a time. According to Microsoft, the execution policy “helps users to set basic rules and prevents them from violating them unintentionally.”
Important Things to Keep in Mind About Execution Policies
On Microsoft Windows computers, you have the choice of setting up an execution policy either for the current user who’s logged in, the local computer, or for a specific session. This gives you more control over managing the execution policies. Since I brought up management of policies, I should point out that you can use Group Policy to configure execution policies for either your computers or users.
If you are a security conscience person like me, you should consider setting execution policy just for the session. This will allow you to run PowerShell scripts during a session but once the session is closed, no one will be able to run scripts on the computer.
Default Execution Policy on Windows Computers
The default execution policy on Windows servers is RemoteSigned. The default execution policy on Windows client computers is Restricted, which means you can run individual commands, but are not allowed to execute a PowerShell script. Therefore, PowerShell scripts cannot run on a Windows client, such as Windows 10, unless you modify the default execution policy. The execution policy effects only the local user and is stored in the Windows registry under HKEY_CURRENT_USER.
The common PowerShell files that you typically execute on Windows computers are the PowerShell profile files that end with extension .ps1. Other PowerShell files include the configuration files with extension .ps1xml and the module script files .ps1m.
As I mentioned, by default the execution policy on Windows 10 clients is configured as Restricted for the Current User scope. You can follow the steps below to change it to RemoteSigned.
Changing Default Execution Policy
If you want to run PowerShell scripts on Windows 10, you need to change the default execution policy. There are many ways to start PowerShell. For example, you can start PowerShell by using the Windows PowerShell app (Windows Search -> Windows PowerShell) or Windows PowerShell ISE console (Windows Search -> Windows PowerShell ISE). Start the console as an administrator (Right-click -> Runs as administrator).
-
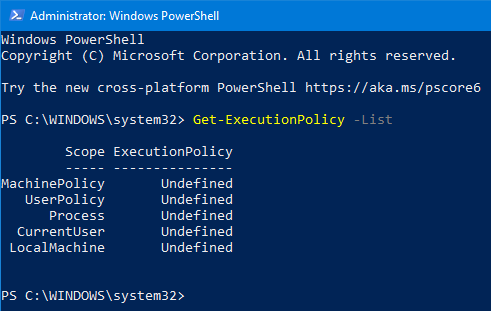
- To view the list of execution policy and their scope use the command Get-ExecutionPolicy -List. There five different scopes, which are listed in the order of precedence. If the policies were defined for multiple scopes, the scope for UserPolicy would take precedence over Process and the CurrentUser would take precedence over the LocalMachine. Visit this link for more information on scopes.
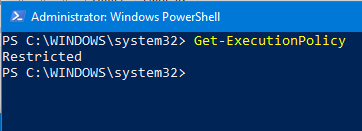
- To see which policy is currently in effect, use the command Get-ExecutionPolicy. The default policy (Restricted) is listed.
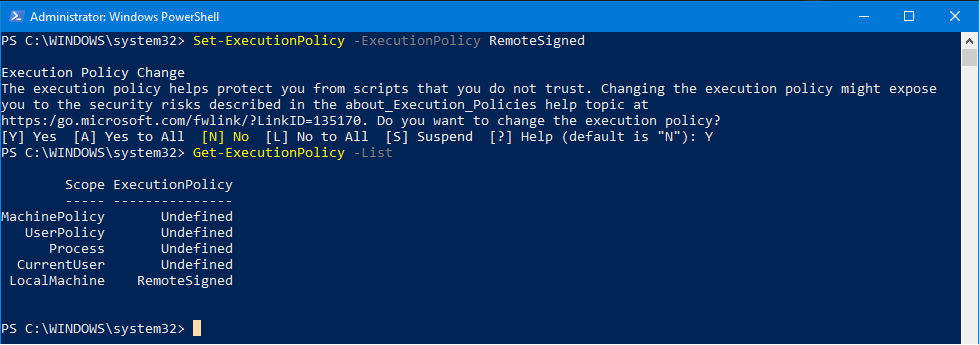
- To be able to run the PowerShell scripts, use the command Set-ExecutionPolicy -ExecutionPolicy <PolicyName>. For example, Set-ExecutionPolicy -ExecutionPolicy RemoteSigned.
- When prompted to change the policy, answer Y for yes and press Enter. You can then look at the scope of the policy by using the command Get-ExecutionPolicy -List. Notice the scope affects the Local Machine so the scripts will run on this computer. When you are done running your script(s) and don’t have a need to run more scripts in the near future, you can go back and change the policy to Restricted as a precaution.
- To remove the above policy for LocalMachine, use the command Set-ExecutionPolicy -ExecutionPolicy Undefined -Scope LocalMachine.
- To view the list of execution policy and their scope use the command Get-ExecutionPolicy -List. There five different scopes, which are listed in the order of precedence. If the policies were defined for multiple scopes, the scope for UserPolicy would take precedence over Process and the CurrentUser would take precedence over the LocalMachine. Visit this link for more information on scopes.
There’s much more you can do with the execution policies. Visit this link to learn more.
| Thanks for reading my article. If you are interested in IT consulting & training services, please reach out to me. Visit ZubairAlexander.com for information on my professional background. |
Copyright © 2021 SeattlePro Enterprises, LLC. All rights reserved.


