Vulnerability in SSL/TLS Could Allow Information Disclosure

Microsoft recently posted this Knowledge Base article 2588513: Vulnerability in SSL/TLS could allow information disclosure. The actual Security Advisory is posted here. According to the advisory:
“Microsoft is aware of detailed information that has been published describing a new method to exploit a vulnerability in SSL 3.0 and TLS 1.0, affecting the Windows operating system. This vulnerability affects the protocol itself and is not specific to the Windows operating system. This is an information disclosure vulnerability that allows the decryption of encrypted SSL/TLS traffic. This vulnerability primarily impacts HTTPS traffic, since the browser is the primary attack vector, and all web traffic served via HTTPS or mixed content HTTP/HTTPS is affected. We are not aware of a way to exploit this vulnerability in other protocols or components and we are not aware of attacks that try to use the reported vulnerability at this time. Considering the attack scenario, this vulnerability is not considered high risk to customers.”
There are at least two mitigating factors:
- The attack must make several hundred HTTPS requests before the attack could be successful.
- TLS 1.1, TLS 1.2, and all cipher suites that do not use CBC mode are not affected.
Workaround
Microsoft offers the following workaround. In Windows 7, disable the TLS 1.0 protocol and enable TLS 1.1 and TLS 1.2 because they are not affected. Unfortunately, in Windows XP the Internet Explorer doesn’t offer TLS 1.1, or TLS 1.2.
NOTE: Neither Mozilla Firefox nor Chrome supports TLS 1.1 and TLS 1.2. Therefore, your best bet is to use Internet Explorer 9 on Windows 7 or Opera 10, which also supports TLS 1.2.
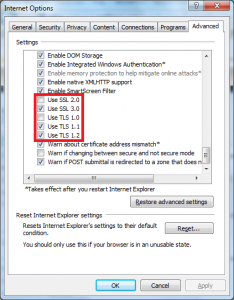
In Internet Explorer 9, go to Tools, Internet options, and on the Advanced tab clear the TLS 1.0 check box and select the TLS 1.1 and TLS 1.2 check boxes. Your screen should look something like this.
Does Fix It Really Fixes Things?
If you use the Fix it solution in the KB article that automatically creates a restore point and then supposedly fixes the problem, you will notice that it DOES NOT clear the TLS 1.0 box. I am not sure why when the entire hoopla has to do with TLS 1.0 and SSL 3.0 in the first place. All it does is enable TLS 1.1. Perhaps enabling TLS 1.1 takes precedence and therefore TLS 1.0 is not used but I don’t feel comfortable using any scripts or wizards created by a vendor because there is no way for me to know exactly what the wizard does behind the scenes. Besides, I have been burned in the past by one of Microsoft’s wizard that installs a security template so I am pretty hesitant when it comes to wizards. I’d much rather make the change manually so I can reverse the process manually if necessary.
One challenge that you might have to face is whether the Web sites you visit support TLS 1.1 and later or not. Until there is a solution (remember this is only a workaround) I would rather implement the workaround just to be on the safe side and take my chances with Web sites not supporting the newer version of TLS.
As a best practice, always sign out of the Web site and then close your browser to ensure that your SSL/TLS session is properly terminated.